Misc
1
签到题
2
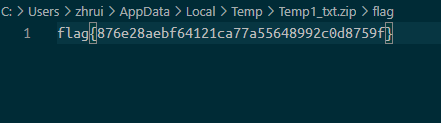
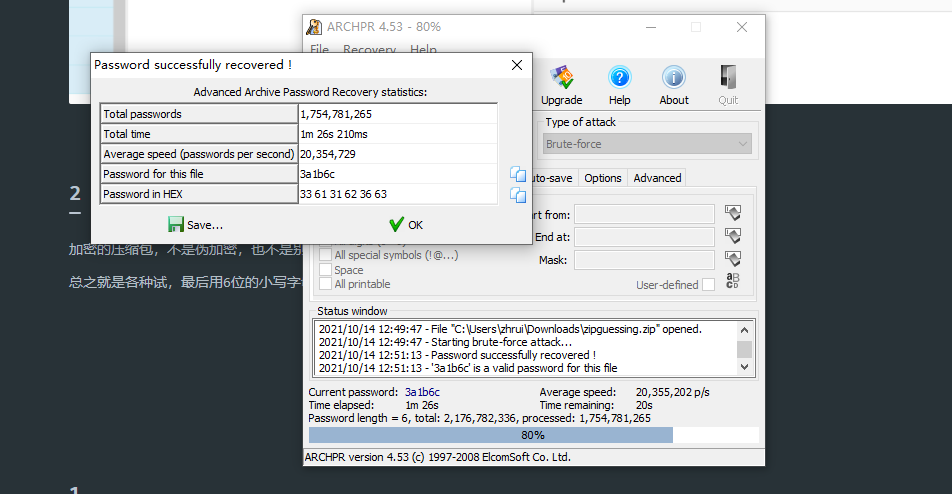
加密的压缩包,不是伪加密,也不是别的加密,尝试通过1-8位的数字,但是没有爆破成功。
总之就是各种试,最后用6位的小写字母加数字成功爆破
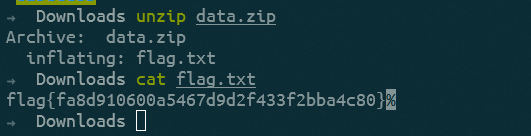
解压后拿到flag
Crypto
3
USB题目
导出usbdata
1 | tshark -r out.pcapng -T fields -e usb.capdata > usbdata.txt |
观察数据,发现只有2位。。。而传统的usb键盘是八位,鼠标是四位。。。。

看了官方的wp,通过观察数据,发现数据有效位只有最后两位,前两位表示是否按下shift(这里脑洞不过去,似乎就做不出来了),由于flag最终是md5,所以,可以不用管是否按下了shift(拿到最终结果小写,然后方括号替换为花括号)
exp利用之前题目的,修改一下长度判断、字典key值判断就行
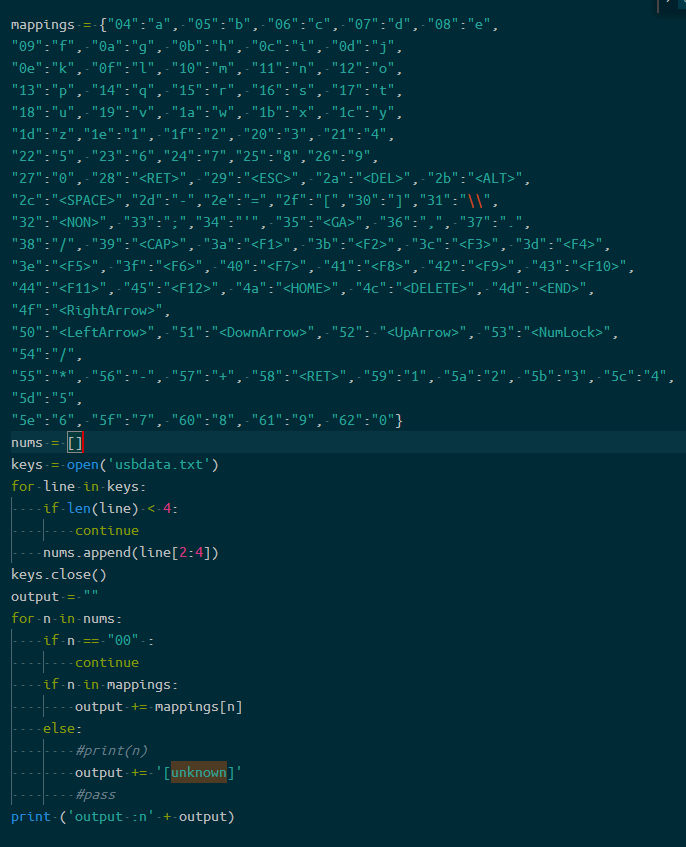
记录一下比较全的映射
1 | mappings = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", |
1
二进制转ascii
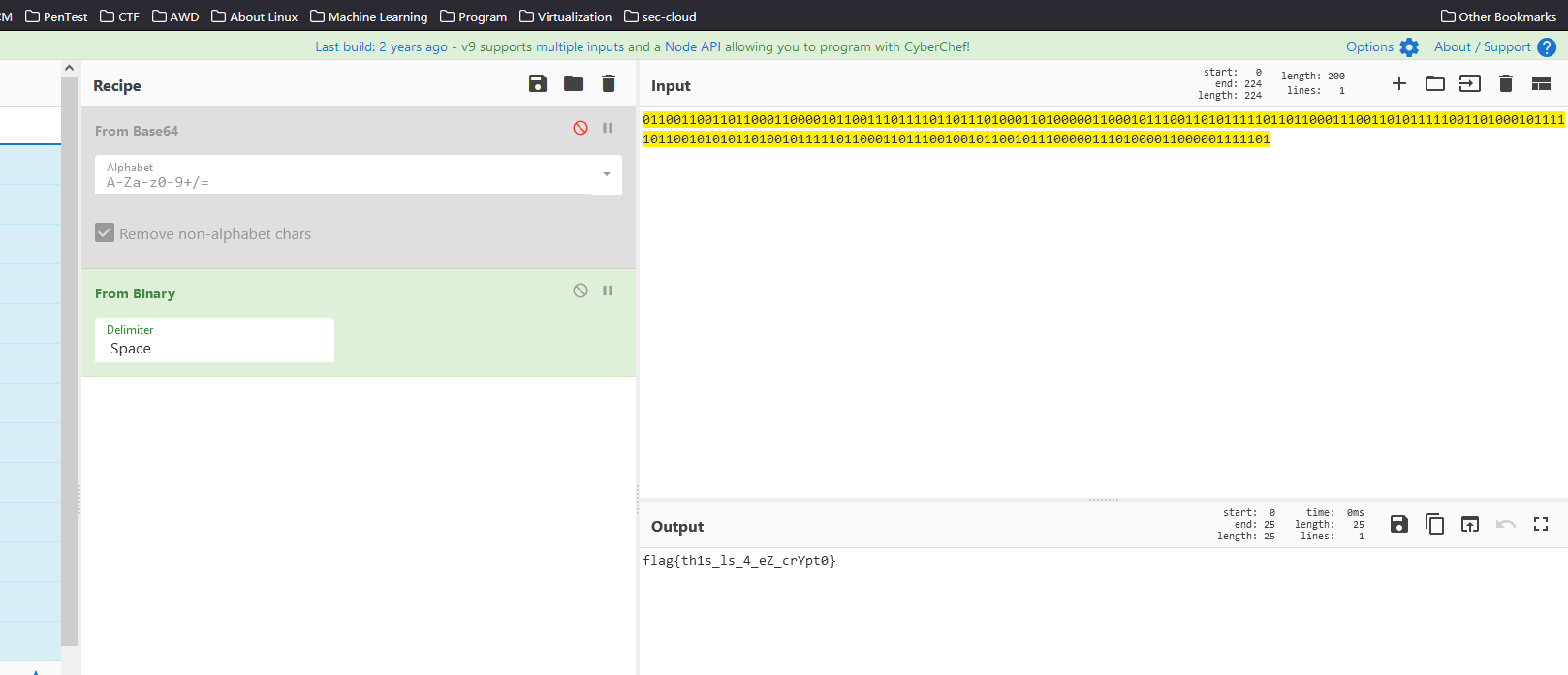
4 | 没做出来
源码两次加密flag,第一层用共模攻击,解除明文
1 | import time |
p泄露了824个低位。。。。。卡在这里,之前只做过p泄露高位的。。。。
Web
1
查看源码发现flag,但是提交报错,以为环境问题后俩才知道是姿势不对。
页面提示input signin

尝试输入Signin,发现页面回显flag在哪
查看头,找到flag
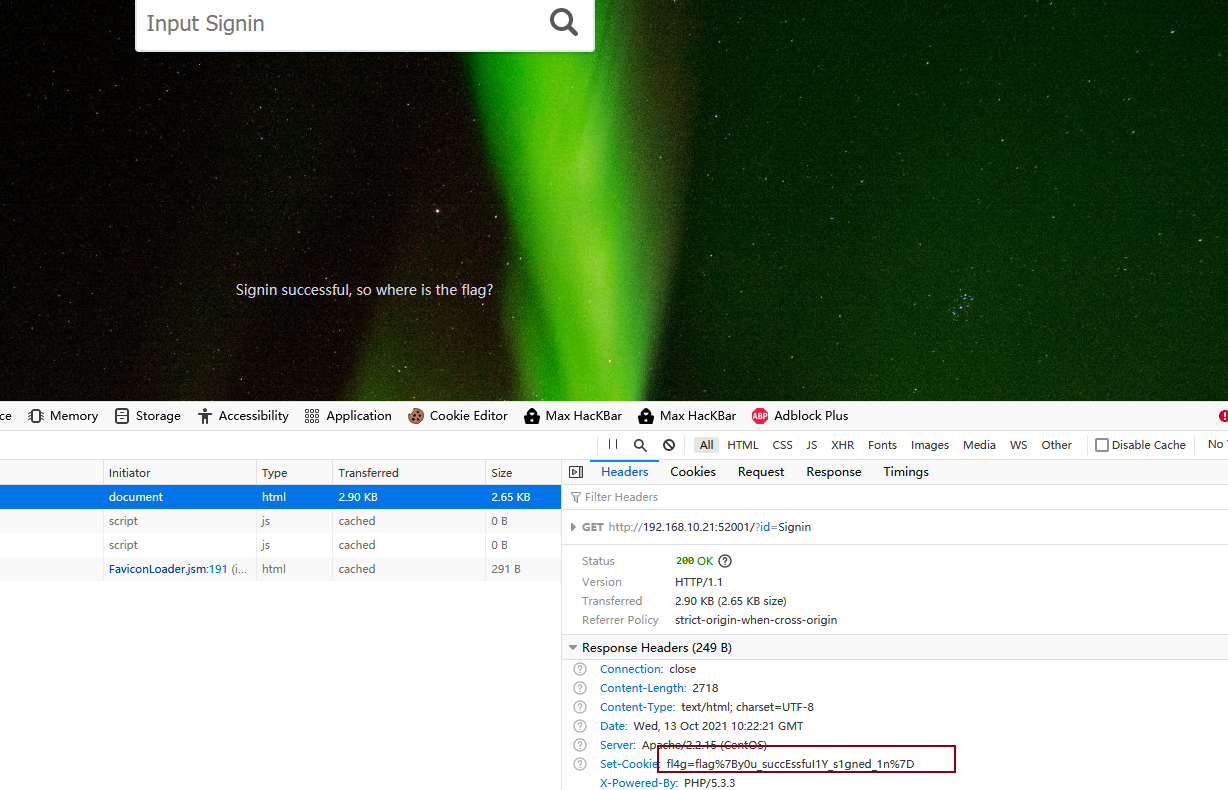
2
输入绕过md5判断
1 | http://192.168.10.22:52002/pony.php/?a[]=1&b[]=2&pony=phpinfo(); |
查看php信息,发现禁用了几乎所有的函数。
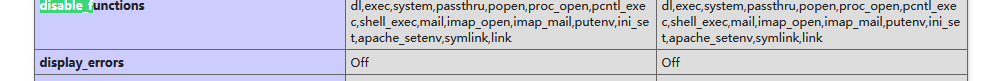
尝试了一圈,没发现能够拿到flag的方式,最后考虑用蚁剑的disable_function绕过,拿到flag
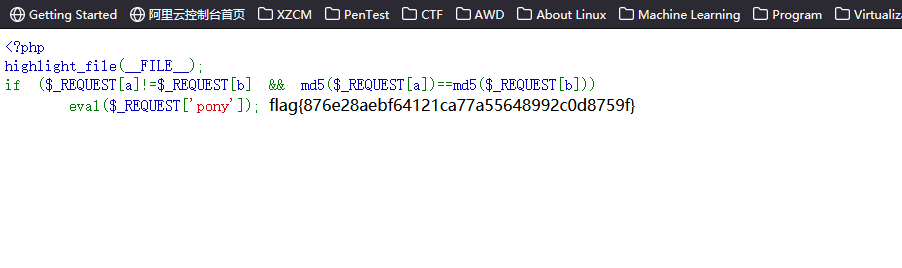
3
1 |
|
4
反序列化题目
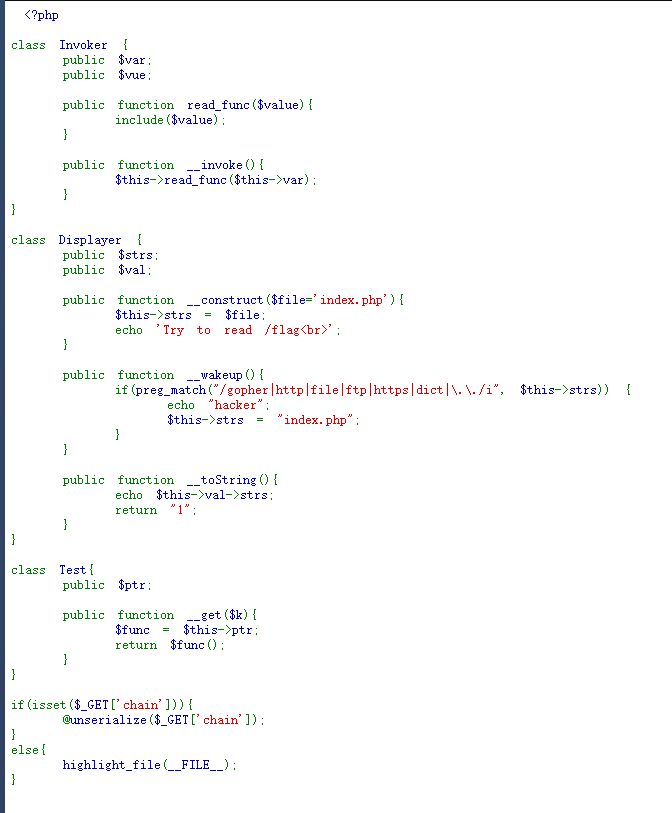
题目提示读取到/flag,现在需要构造反序列化的ROP